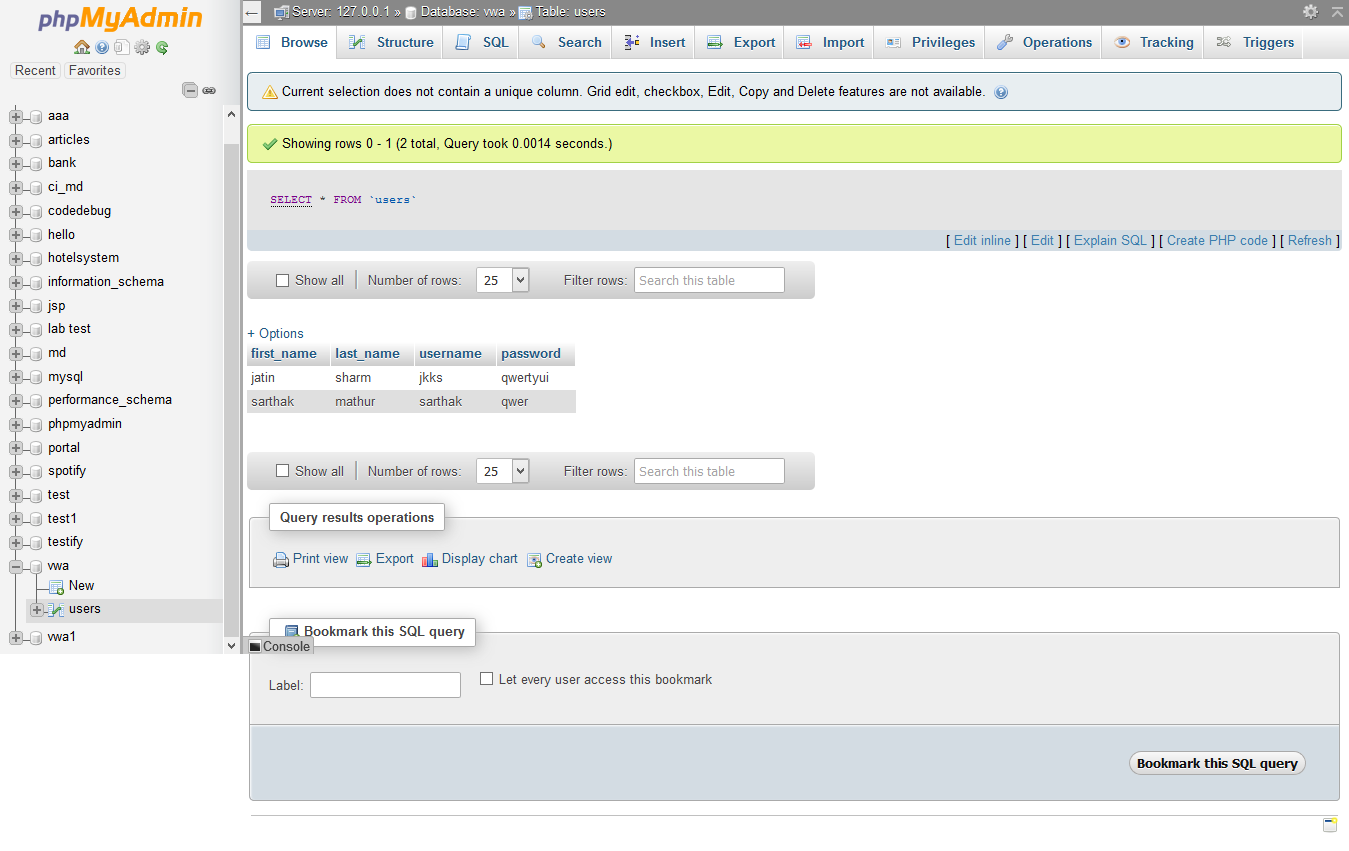
- Create a database as
VMAand create a tableusersin it with following fields :
- first_name
- last_name
- username
- password
-
Visit localhost/security/sinin1.html. Set username and password as
' ' OR '1' = '1'. After this, login will be granted of some random user without username and password. -
If we enter some particular username and password as
' ' OR '1' = '1', login will be granted of that particular user without password. -
To delete the entire table, use the query :-
' UNION DROP TABLE USERS --;. -
For prevention of this, we can use the function :-
mysql_real_escape_string(). Adding these 2 lines will remove the special characters from input.
$Fname = mysqli_real_escape_string($conn, $Fname);
$Password = mysqli_real_escape_string($conn, $Password);